Fortress Salesforce: A Guide to Impregnable Salesforce Security
In today’s digitally driven landscape, protecting your Salesforce data is paramount. As a leading cloud-based CRM platform, Salesforce empowers businesses to manage customer interactions, but robust security measures are essential to mitigate risks and safeguard sensitive information. This blog delves into Salesforce security best practices, equipping you to create an impenetrable fortress around your valuable data.
Understanding the Threat Landscape
Before embarking on your Salesforce security journey, it’s crucial to recognize the potential adversaries:
- Cybercriminals: These malicious actors employ a range of tactics, from phishing attacks and malware to social engineering, to gain unauthorized access to data.
- Accidental Insider Threats: Unintentional data breaches can occur due to human error, such as sharing login credentials or neglecting to follow security protocols.
- Negligence: Lax security practices, like weak passwords or inadequate access controls, can leave your data vulnerable.
The Bedrock of Security: Core Principles
There is a set of foundation principles that help us construct Salesforce security best practices. These include:
- Defense in Depth: Implement multiple layers of security to create a robust barrier against breaches. Even if one layer is compromised, others can still hinder attackers.
- Least Privilege: Grant users only the minimum level of access required to perform their jobs. This minimizes the potential damage caused by unauthorized access.
- Data Encryption: Encrypt sensitive data both at rest and in transit to ensure confidentiality even if intercepted.
- Continuous Monitoring: Regularly monitor user activity, system logs, and potential security vulnerabilities to identify and address threats promptly.
- Security Awareness Training: Educate your users about cyber threats, best practices, and how to report suspicious activity
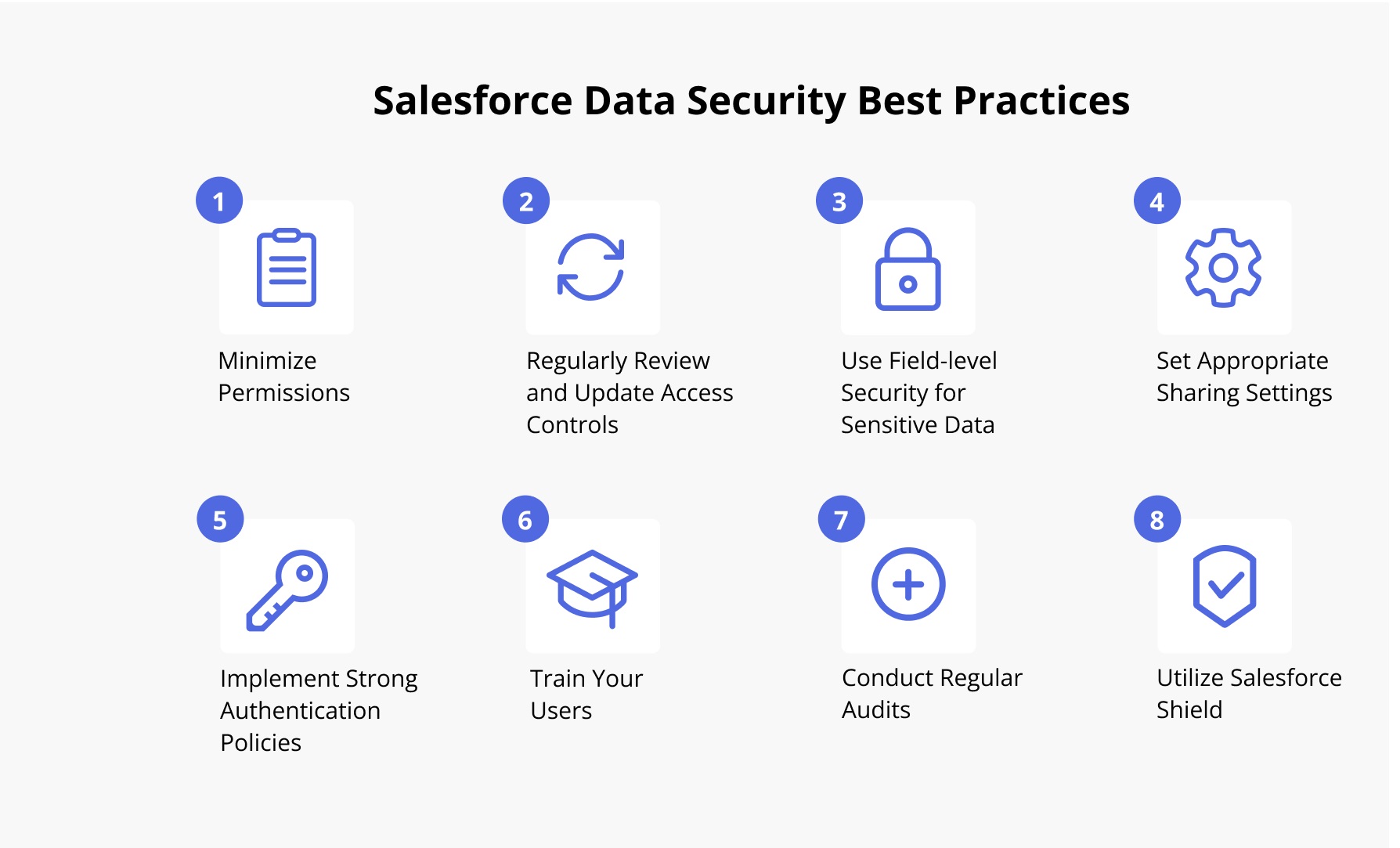
The Arsenal of Security: Essential Practices
- Multi-Factor Authentication (MFA): Add an extra layer of protection beyond passwords by requiring a secondary verification step, such as a code from an authenticator app.
- Strong Password Policies: Enforce complex passwords with a minimum length, character variety, and regular password changes to deter brute-force attacks.
- IP Address Restrictions: Limit login attempts to designated IP addresses, typically within your corporate network or VPN, to prevent unauthorized access from outside locations.
- Session Management: Set session timeout limits to automatically log out inactive users, reducing the risk of unauthorized access if a device is left unattended.
- User Access Controls: Utilize profiles and permission sets to grant users access to specific data and functionalities based on their roles. Periodically review and update access privileges to ensure continued appropriateness.
- Field-Level Security: Control visibility and editability of specific data fields within objects, ensuring users only see and modify what’s pertinent to their tasks.
- Data Encryption: Leverage Salesforce Shield Platform Encryption or Data Loss Prevention (DLP) to encrypt sensitive data both at rest and in transit, rendering it unreadable even if intercepted.
- Event Monitoring and Logging: Enable comprehensive event monitoring to track user activity, login attempts, and data modifications. Maintain detailed logs for forensic analysis and anomaly detection.
- Regular Security Audits and Penetration Testing: Conduct periodic salesforce security assessments to identify and address potential vulnerabilities. Penetration testing simulates real-world attacks to evaluate your defense’s effectiveness.
- Backup and Disaster Recovery: Establish a robust backup and disaster recovery plan to ensure business continuity in case of unforeseen events like data loss or system outages.
- Security Awareness Training: Educate your users on common cyber threats, phishing schemes, Salesforce security best practices, and the importance of reporting suspicious activity.
- Third-Party App Security: Scrutinize third-party apps integrated with Salesforce to ensure they adhere to robust security standards.
Continuous Vigilance: Maintaining Impregnable Security
The battle for data security is an ongoing one. Threats evolve, and so must your defenses. Here’s how to remain vigilant:
- Stay Informed: Regularly keep yourself updated on the latest security threats and trends to adapt your security measures proactively.
- Embrace New Technologies: Leverage advanced security tools and features offered by Salesforce to stay ahead of potential threats.
- Foster a Security Culture: Create a culture of security awareness within your organization, where everyone plays a role in protecting data.
By following these comprehensive Salesforce security best practices and maintaining a culture of vigilance, you can construct a formidable fortress around your data, ensuring its integrity, confidentiality, and availability.